Hopefully when you received a phishing email regarding one of your online accounts you didn’t click the link and try to login. This is how hackers attempt to gain access to your account without you knowing. If you did login, immediately close your browser. Then, re-open it and go to the proper sign page through your browser and change your password.
We all get phishing attempts via email but we can do more than just educate ourselves on how to prevent being tricked. Before you delete the phishing email report it to the proper website that the phishing email is trying to access. These same companies have cyber security people that you can forward the email to. Simultaneously you can report all phishing attempts to the Anti-Phishing Working Group at [email protected]
When concerned about possible virus infection of your computer perform a malware scan. To clarify, most phishing attempts are not created to infect and take over your computer. Rather, the goal of phishing is to learn your account login details so they can steal your personal information.
Below are some of the more common companies that identity thieves try to mimic. These are just examples and there are many others. If you don’t see the contact information below for the company you are looking for, simply Google it safely at the top of our website. For example, if the phishing attempt is in regards to PayPal, Google “Report PayPal Phishing”. Often, you will find an email address posted that you can forward the phishing email to.
Report as Phishing to These Companies
In addition to forwarding phishing emails to appropriate companies and to the Anti-Phishing Working Group, you can also report the phishing link to Google but be careful. Don’t open the link in a browser, simple right click the link and select copy hyperlink. Cut and paste that link into the Google submission form and submit. Then, delete the phishing email.
Here are a few examples of the top companies whose account holders are the top targets. These companies want you to forward phishing emails to them so they can prevent future fishing attacks.
PayPal
PayPal is a top target of phishing because it gives thieves direct access to your money. If if you don’t currently have funds in your PayPal account, people with access can make payments out of a bank account or credit card that you have linked to. Report PayPal phishing attempts to [email protected] which can also be accessed on their PayPal suspicious activity.
If you have clicked a bad link or are worried about whether your account has been compromised change your password immediately. Learn more about how PayPal deals with account fraud.
DocuSign
Often, phishing links for DocuSign will go to Google Docs. This may appear legitimate because it is using the Google domain but really it is someone with a Google account hosting a bad doc to gain your personal information. Be proactive and report suspicious emails to DocuSign’s security team at [email protected]. If you feel the security of your account is at risk, contact DocuSign customer support.
Below are some tips to help spot the difference between real and spoof DocuSign emails:
All URLs to view or sign DocuSign documents will contain “docusign.net/” and will always start with https. All legitimate DocuSign envelopes include a unique security code at the bottom of notification emails. If you do not see this code, don’t click on any links or open any attachments within the email.
For the latest DocuSign security and system performance information, visit the DocuSign Trust Center.
Report Facebook Phishing
Facebook is one of the largest website in the world with over 2.7 billion active users. They have taken great strides to protect against phishing and promote that they take seriously all phishing reports when you forward the email to [email protected]. They have also set up security tools to prevent outsiders from signing into your account. Like many online accounts they recommend and offer ‘two factor authentication’. They will also email you of suspicious login attempts when you set up to receive unrecognized login notifications.
Netflix
Because Netflix is such a popular streaming service these days, it’s one of the more popular targets for phishing. Netflix states that they will never ask you to click a link to enter personal information about your account. Even if you are not sure the email you receive is a phishing attempt, report it to Netflix by forwarding the email to [email protected]. If you want to check your account to see if something is wrong with your billing, for example, go to Netflix.com directly or via a bookmark you’ve already saved to log into your account.
Here is a classic phishing email that Netflix would never send to you.
Dear user, We’re having some trouble with your current billing information. We’ll try again, but in the meantime you may want to update your payment details.
Most phishing emails feature proper links to the company at the bottom of the email, such as the Netflix support page or contact page. This is to trick you into thinking it’s legit. However, the link in the middle of the email goes to a different website.
Banks and Credit Card Companies
You may only have one bank account and one credit card. So when you receive an email from a bank that you don’t have an account with, it’s easy to ignore. You may even be thinking, why would they send this to me? Well, cyberthieves use spam internet servers to sent the phishing email to millions of people because they know at a percentage of those on the list will have an account with a particular bank.
This is why you will sometimes get an email that looks like it’s from your bank. Don’t worry, the scam artist probably doesn’t know you have an account with a certain bank. You are simply one of millions of people on a list.
Chase is one of the top banks that phishing emails try to mimic. But really, there are too many banks and credit card companies to list, so it’s wise to be wary of any email from your bank. Any information you need to know about your bank account will be within your account, so just go to your regular bookmark in your browser to login or to go Google and search for your bank. You never have to worry if you always go directly to your bank to see if there are any important notifications for you. Or just call you bank.
To report a phishing email to your specific bank, search for your financial institution on Google by typing in your bank name followed by the keywords ‘report phishing email’.
Report as Phishing to Apple
Apple is a big one. Your user name and password gives phishing attempts access to your iCloud account where all of your files are stored, including your contacts and pictures. If you see any email that looks suspicious report it to Apple by forwarding the email to [email protected]. Apple will never ask you to verify your identity using your password. They also recommend to protect your Apple ID by using two-factor authentication. This security measure is available with many online accounts where a code is sent to you via text or email to complete your login. This means that even if hackers gain access to your user name and password and try to log in, you will get a notification, but unless they have access to your phone, they can’t gain access.
Courier Companies and Shipping Outlets
Couriers include companies like Fed Ex, UPS, DHL Express, Purolator, and USPS. Shipping may also come from online stores who use couriers, such as Amazon and Target. The email may say something line “We are having trouble delivering your shipment!” If you are expecting a shipment, you will immediately be concerned. If you are not expecting a shipment you may wonder why you are receiving a product when you didn’t order anything. This is probably a phishing email, but even if it isn’t look closely at the email. It’s always best not click any links and simply go to your account directly through your browser. If you don’t have an account with a specific store, such as Walmart, then you know it is more than likely a phishing email. Report it to the company concerned then delete the email.
Amazon
Many people have an Amazon account. You may get an email from Amazon asking for your to login to correct a problem. This is more than likely phishing. Do not login using the link in the mail. Go directly to your Amazon account from your browser to see if there are any issues. Amazon also uses couriers and the same safety rules apply. Amazon usually notifies online shoppers that a real shipment has been delivered to their door, but they will never put a link in that email and ask you to check on your shipment. Forward all suspicious emails to Amazon at [email protected]
Additional Contacts to Report Phishing
If you have scrolled down to this bottom of this email looking for a company that is not listed above, below are are few safe links or email addresses to report a phishing attempt to that company. Reporting phishing is important so that collectively, we can work to shut down the hackers and scammers who are trying to steal personal information from millions of account holders around the world.
A Quick Review of What to Do When you Receive a Suspected Phishing email.
- Don’t click any link to login to your account. Go directly to your account via your browser bookmark or by searching for it on Google. If you don’t have an account related to the email, it’s probably a phishing attempt and you have nothing to worry about.
- Before deleting the phishing email, forward the email to the company the identity thieves are pretending to be.
- Report the phishing link to Google but be careful how you copy the link to paste it on Google’s reporting page. Never click the link. Instead, right click on the link to copy the hyperlink. Then delete the email.
- When you forward a phishing email to any company, cc the email to the Anti-Phishing Working Group at [email protected]
Here are additional emails not written about above that you can report phishing emails to:
Report Email as Phishing to Gmail
This image below shows you how to report amy phishing attempt that is sent to your Gmail. To access this, you need to be signed into the web version of your gmail account. Reporting these emails will help reduce phishing and spam emails to your Gmail, but you should also report emails to the company being spoofed.
To report phishing to Gmail follow the steps below. 1) On an open email, select the drop down menu on the top right. 2) Select Report Phishing.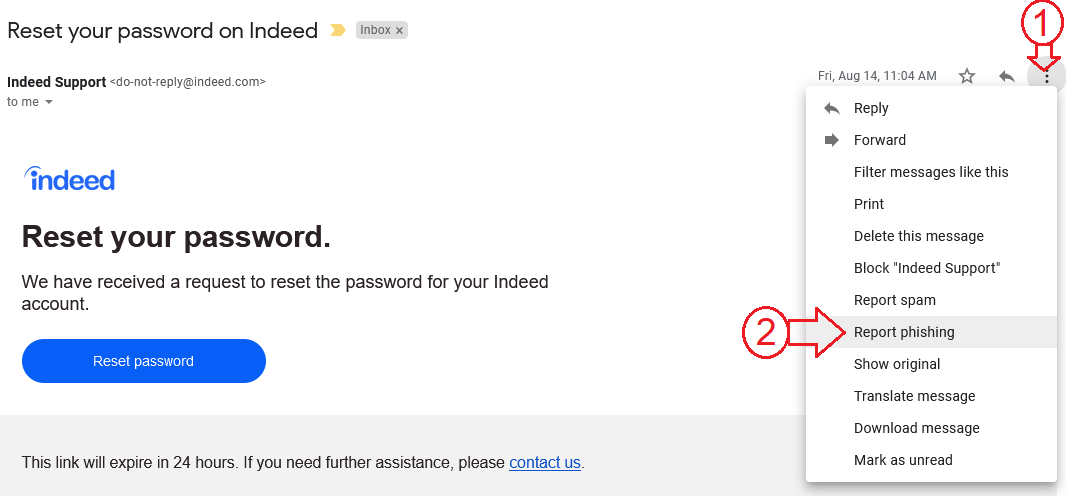
About Google Account Security: Since Google accounts only have one login to multiple website, including YouTube and the multiple apps within Google for Education, consider setting up Two Factor Authentication to protect your account.
Additional Resources
Make sure your computer is not infected with Malware because you clicked a phishing email, scan your computer and protect against future attacks.
Learn more about Phishing and the new ways hackers use to steal peoples personal information. Read about Smishing (Text) and Vishing (Phone) Scams.








